ODS.ODSBriefcaseWebIDGroup
ODS-Briefcase WebID based ACL Sharing to Group Guide
- Configure Virtuoso+ODS instance as an X.509 Certificate Authority and HTTPS listener
- Generate a Personal HTTP based Identifier for fictitious Person Entity: Tom and then bind his personal Identifier to an X.509 Certificate (thereby giving him a WebID)
- Generate a Personal HTTP based Identifier for fictitious Person Entity: Anna and then bind her personal Identifier to an X.509 Certificate (thereby giving her a WebID)
- Log into ODS-Briefcase as user "Demo" (a Person Entity)
-
Create a WebID Protocol Group, for ex.
with name "MyWebIDGroup" and add the users Tom and Anna's WebID's to it:
-- Tom's WebID http://cname/dataspace/person/tom#this -- Anna's WebID http://cname/dataspace/person/anna#this
- Share an ODS-Briefcase hosted resource explicitly with "Tom and Anna" via their Group WebID:
http://<cname>/dataspace/user-name/group/MyWebIDGroup
- For a given resource go to ODS-Briefcase ->Resource->Edit->Sharing tab.
- In the "WebID users" section click the "Add" button in order to add new WebID and set respectively the desired rights.
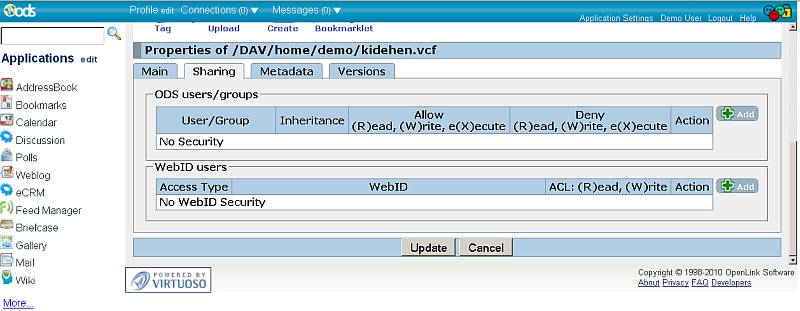
- In the shown form:
- Select for "Access Type": Group
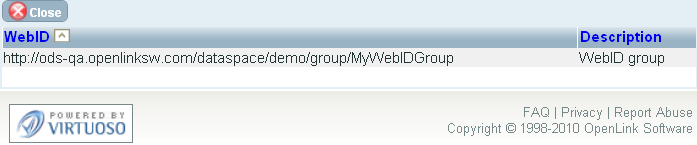
- Enter WebID Protocol Group or selected it from the offered list:
- Set Web Access, for example by checking the (R)ead check-box.
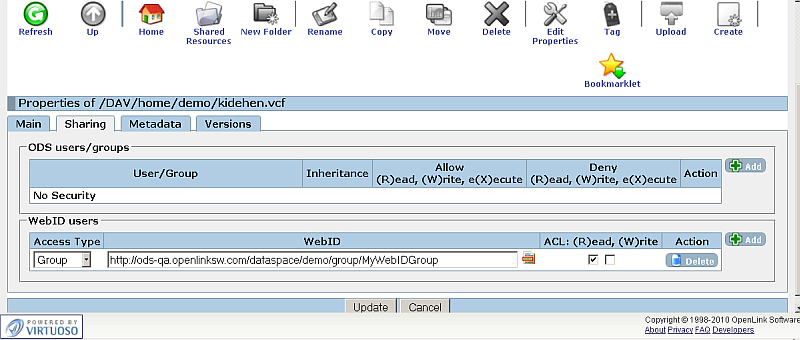
- Click the "Update" button.
- As user which belongs to the WebID Protocol Group "MyWebIDGroup": Tom, attempt to view the resource shared by Person Entity "Demo" by doing the following:
- refresh browser
- access the url: https://host:ssl-port/DAV/home/user-name/user-resource. For this example, it should be: https://localhost:4433/DAV/home/demo/kidehen.vcf
- when prompted by browser, select Tom's Certificate
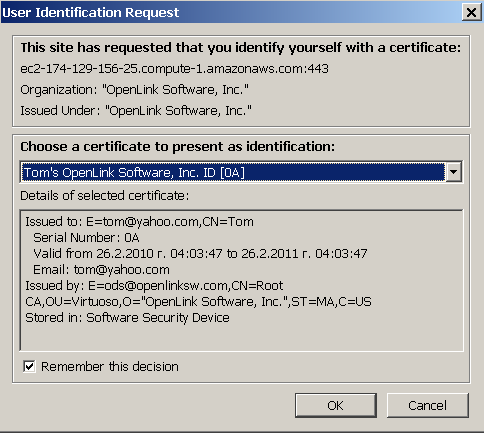
- after successful authentication, you will be able to save or view the shared resource: kidehen.vcf.
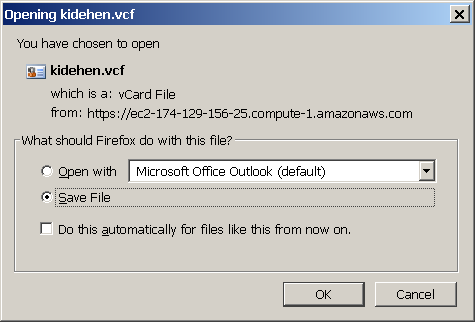
- As user which belongs to the WebID Protocol Group "MyWebIDGroup": Anna, attempt to view the resource shared by Person Entity "Demo" by doing the following:
- refresh browser
- access the url: https://host:ssl-port/DAV/home/user-name/user-resource. For this example, it should be: https://localhost:4433/DAV/home/demo/kidehen.vcf
- when prompted by browser, select Anna's Certificate
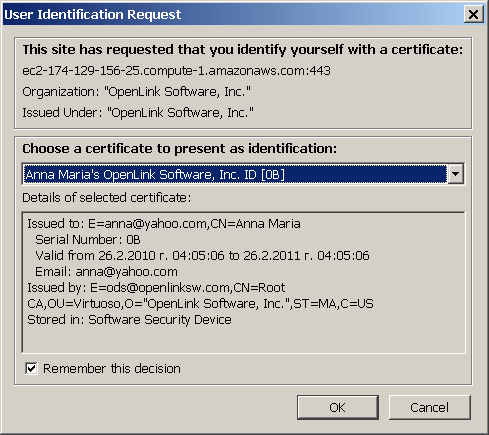
- after successful authentication, you will be able to save or view the shared resource: kidehen.vcf.

References
- Constraining Resource Access To Group Members using SPARQL ASK Query and Web-accessible Linked Data
- Constraining Resource Access Using Social Relationship Semantics and WebID
- Safeguarding your Virtuoso-hosted SPARQL Endpoint
- SPARQL Endpoint Protection Methods Collection
- Virtuoso documentation
- Virtuoso Tips and Tricks Collection
- SPARUL over SPARQL using the http://cname:port/sparql-auth endpoint
- Virtuoso Authentication Server UI
- Manage a SPARQL-WebID based Endpoint
- WebID Protocol Support in OpenLink Data Spaces.
- Manage ODS Datadspaces Objects WebID Access Control Lists (ACLs):
- Guide for Set up a X.509 certificate issuer and HTTPS listener and generate ODS user certificates
- Configure Virtuoso+ODS instance as an X.509 Certificate Authority and HTTPS listener
- Configure Virtuoso instance as an X.509 Certificate Authority and HTTPS listener
- Setting up PubSubHub in ODS
- PubSubHubBub Demo Client Example
- Feed subscription via PubSubHub protocol Example
- Setting Up PubSubHub to use WebID Protocol or IP based control lists
- CA Keys Import using Conductor
- Generate an X.509 Certificate hosted WebID Guide
- Generate an X.509 Certificate (with a WebID watermark) to be managed by host operating system keystore
- Generate an X.509 Certificate (with a WebID watermark) to be managed by a browser-based keystore
- Using Virtuoso's WebID Verification Proxy Service with a WebID-bearing X.509 certificate
- Using Virtuoso's WebID Identity Provider (IdP) Proxy Service with an X.509 certificate
- ODS Briefcase WebID Protocol Share File Guide
- WebID Protocol Specification
- Test WebID Protocol Certificate page
- WebID Protocol Certificate Generation page
