Generate an X.509 Certificate (with a WebID? watermark) to be managed by the Firefox browser-based keystore
Prerequisites
Certificate Generation Process
These steps will work against any ODS instance where you have the requisite privileges.
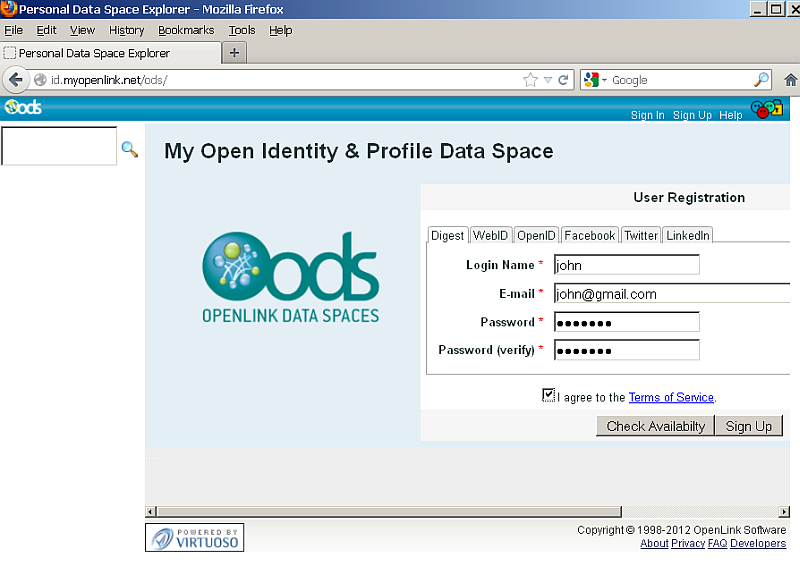
- Go to the ODS home page (local or remote) and log in as an ODS user (registering as such first, if necessary).
- After log in, you will have an ODS-generated Person Entity Identifier (an HTTP URI that Identifies "You") of the form:
http://cname/dataspace/person/user-name#this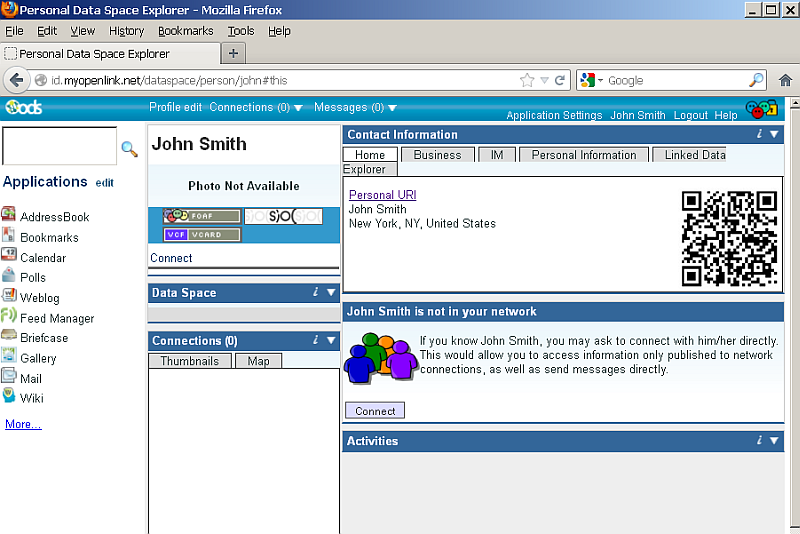
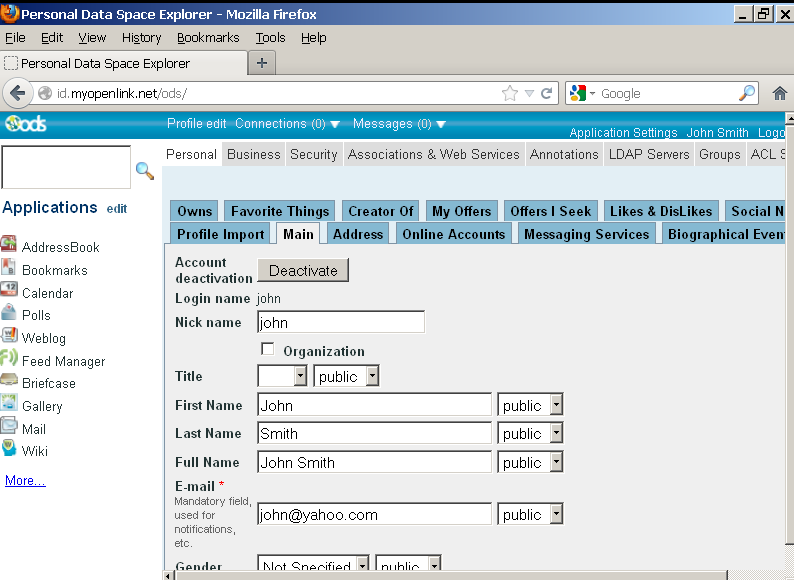
- Fill out your profile, if still in default state.
(Note: If this step is skipped, the resulting X.509 certificate may not have a human-readable name.)
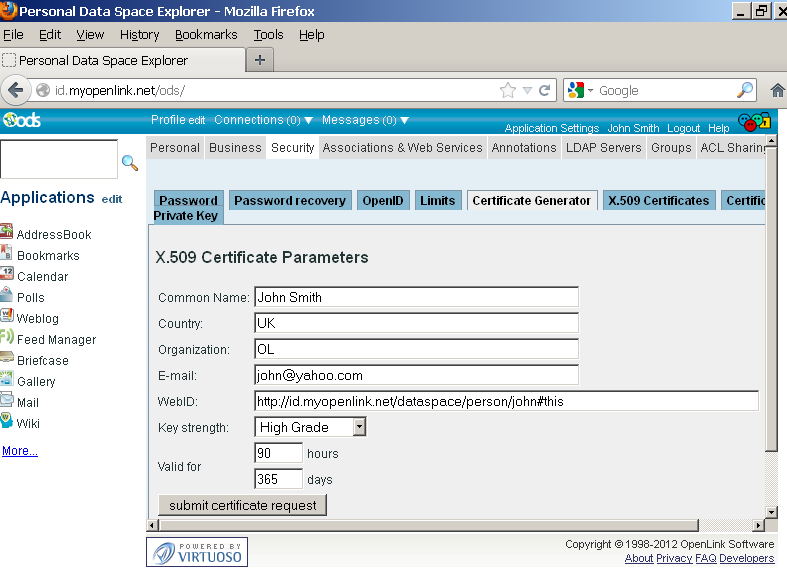
- Go to Security:
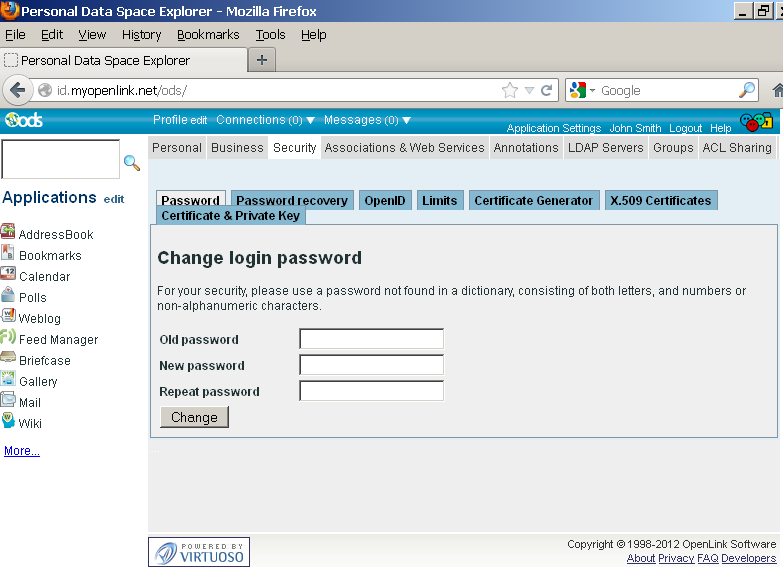
- Go to Certificate Generator:
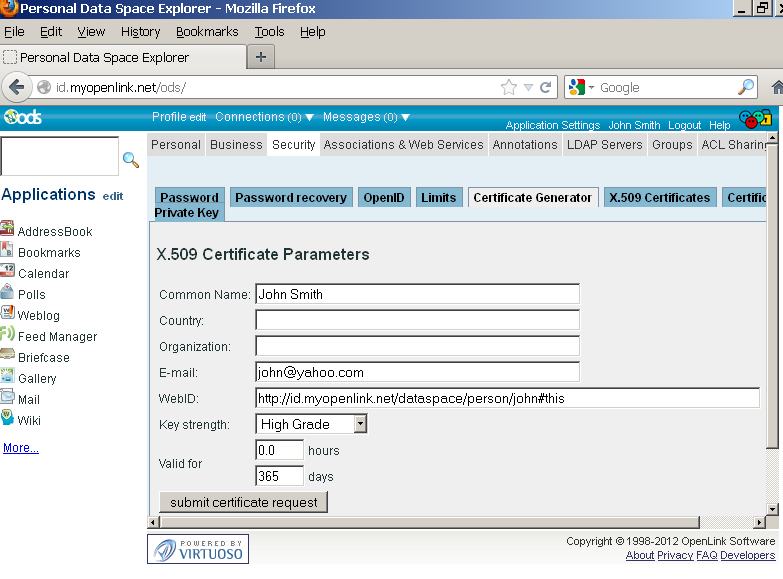
- Fill out the form, for example:
- Click Submit certificate request.
- Firefox should show that it is generating a private key:
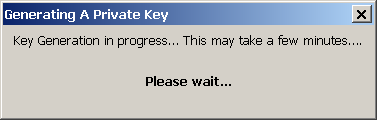
- When private key generation is finished, Firefox should report a successful installation of the certificate:
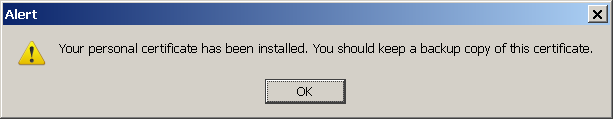
- Go to X.509 Certificates.
- The new certificate should be shown in the list of certificates available for the ODS user:
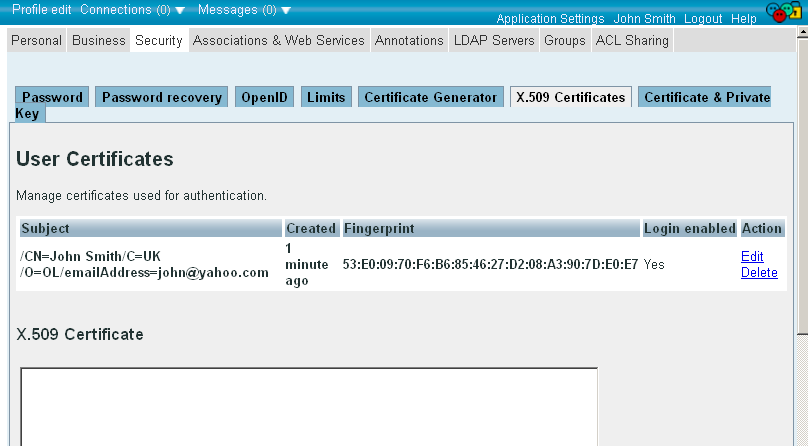
- Note you have now also the option automatic WebID? Login set to enabled -- a powerful feature benefits of which we will demonstrate next in our example:
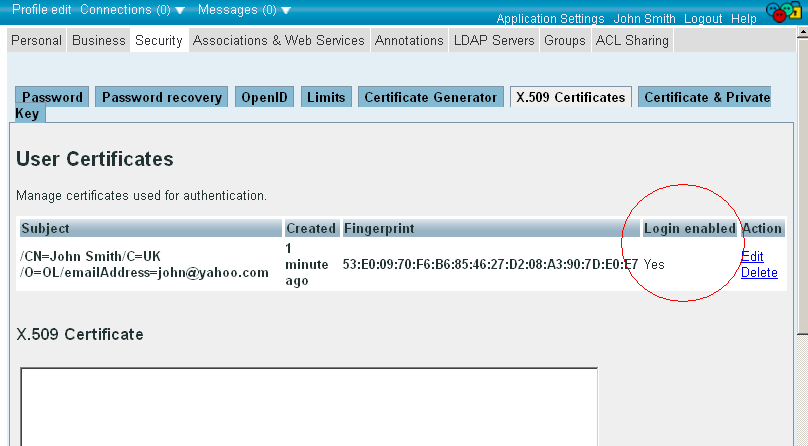
- Verify the new certificate by performing the following steps:
- Log out and access https://id.myopenlink.net/ods/;
- When prompted by your browser, select the new certificate generated above:
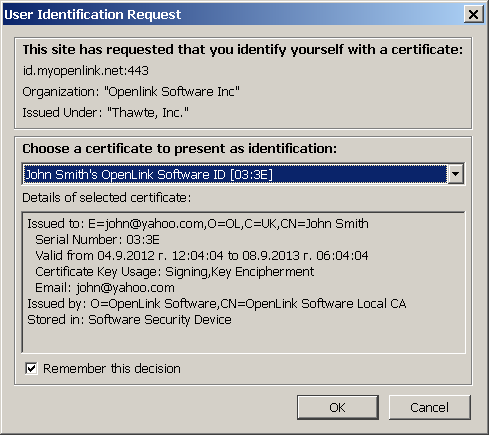
- You should then be presented with the ODS Log-in form.
Click WebID? Login:
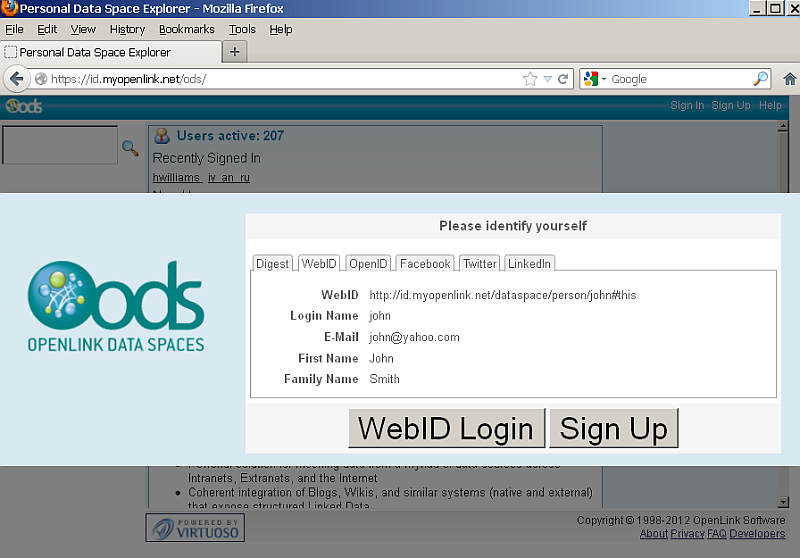
- You should now be successfully logged in:
- If you now log in as another user (e.g.,
demo), you can share a resource to the above user, using a WebID-based ACL, which is itself enabled by the new WebID?-watermarked X.509 Certificate.
Related
- Generating WebID-watermarked X.509 Certificates for Use with ODS
- Generate an X.509 Certificate (with a WebID watermark) to be managed by a browser-based keystore
- Safeguarding your Virtuoso-hosted SPARQL Endpoint
- SPARQL Endpoint Protection Methods Collection
- Virtuoso documentation
- Virtuoso Tips and Tricks Collection
- SPARUL over SPARQL using the http://cname:port/sparql-auth endpoint
- Virtuoso Authentication Server UI
- Manage a SPARQL-WebID based Endpoint
- WebID Protocol Support in OpenLink Data Spaces.
- Manage ODS Datadspaces Objects WebID? Access Control Lists (ACLs):
- Guide for Set up a X.509 certificate issuer and HTTPS listener and generate ODS user certificates.
- Configure Virtuoso+ODS instance as an X.509 Certificate Authority and HTTPS listener
- Configure Virtuoso instance as an X.509 Certificate Authority and HTTPS listener
- Setting up PubSubHub in ODS
- PubSubHubBub Demo Client Example
- Feed subscription via PubSubHub protocol Example
- Setting Up PubSubHub to use WebID Protocol or IP based control lists
- CA Keys Import using Conductor
- Using Virtuoso's WebID Verification Proxy Service with a WebID-bearing X.509 certificate
- Using Virtuoso's WebID Identity Provider (IdP) Proxy Service with an X.509 certificate
- ODS Briefcase WebID Protocol Share File Guide
- WebID Protocol Specification
- Test WebID Protocol Certificate page
- WebID Protocol Certificate Generation page