Generate an X.509 Certificate (with a WebID watermark) that's managed by host operating system keystore: Safari (on Mac OS X Only)
- Set up an X.509 certificate issuer and HTTPS listener.
- Set up X.509 Certificate Service.
- Go to the ODS home page (local or remote) and register new user (or log in as existing ODS user):
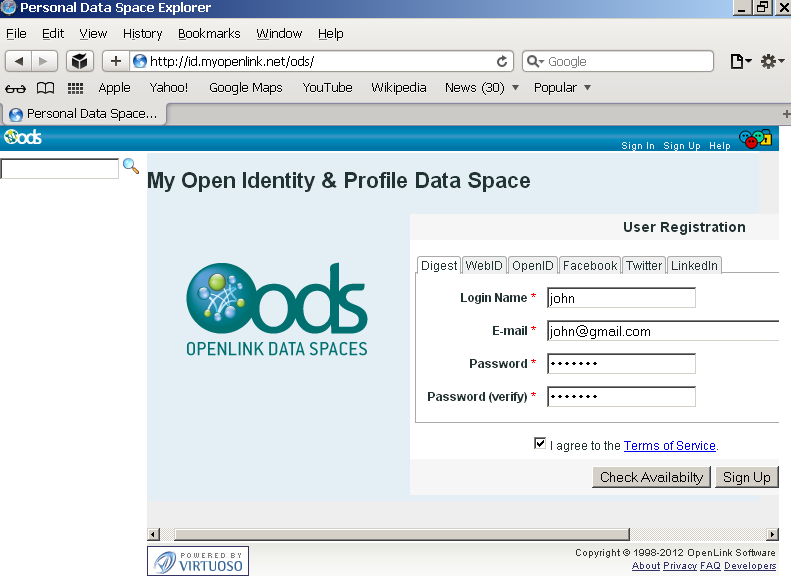
- Post registration you end up with an ODS generated Person Entity Identifier (an HTTP URI that Identifies "You") that takes the form:
http://cname/dataspace/person/user-name#this
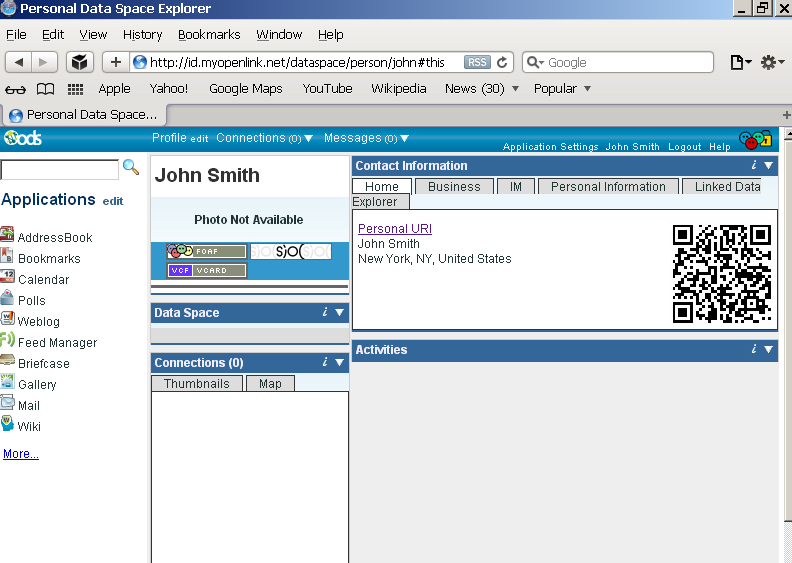
- Edit your profile (Note: If this step is skipped, the resulting X.509 certificate will not have a human readable name):
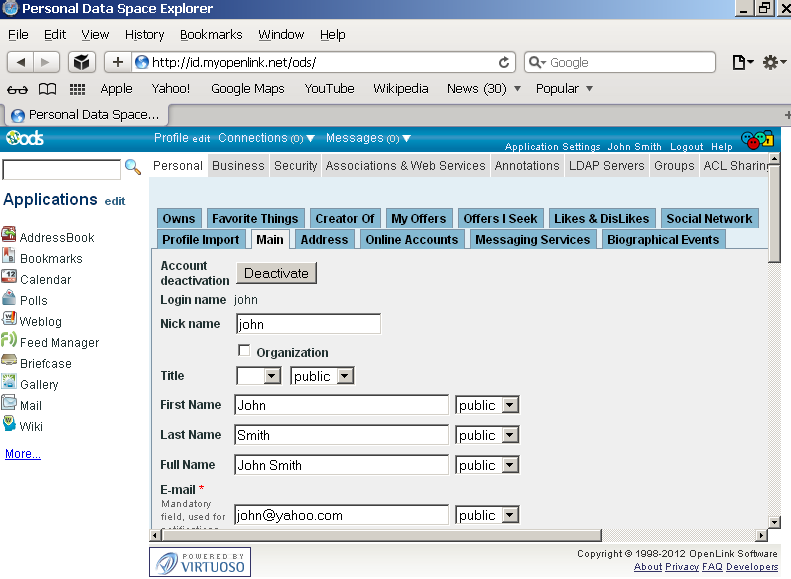
- Go to Profile Edit -> "Security":
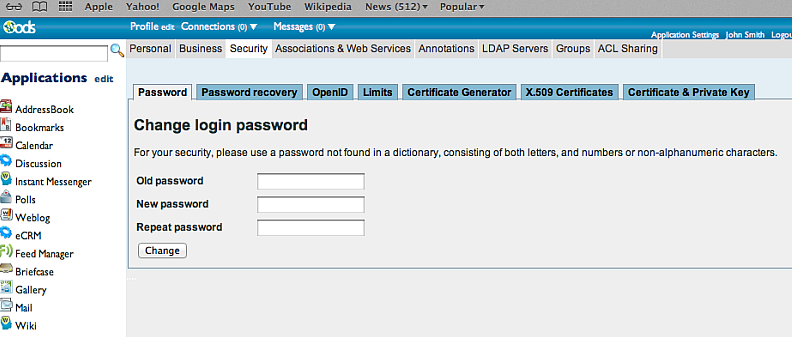
- Go to "Certificate Generator":
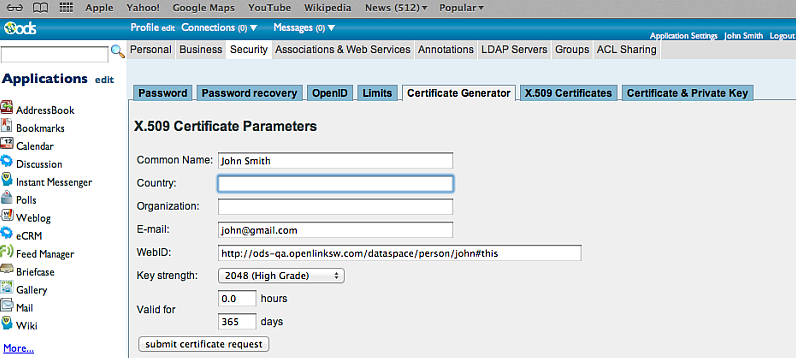
- Complete the certificate details for the user:
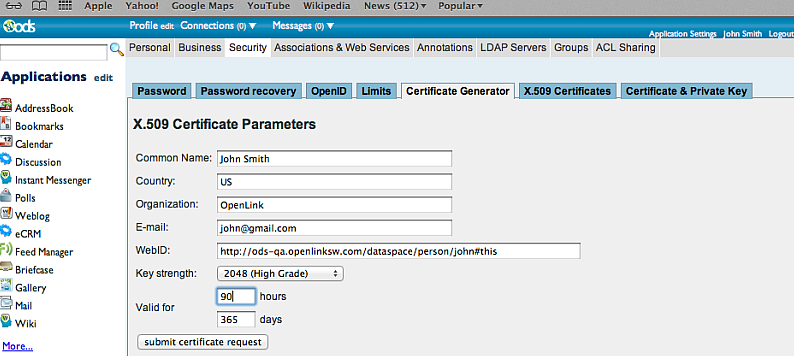
- Click "Submit Certificate Request" to generate the certificate.
- The Mac OS X key chain is automatically loaded with the new certificate loaded:
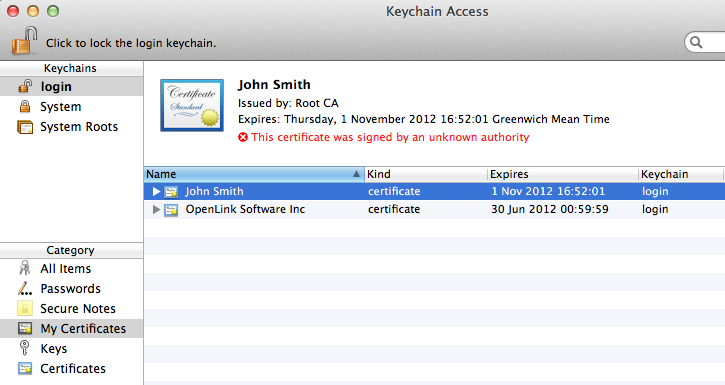
- The certificate is "untrusted" in the key chain by default and needs to be set to trusted by.
- Specify Certificate details:
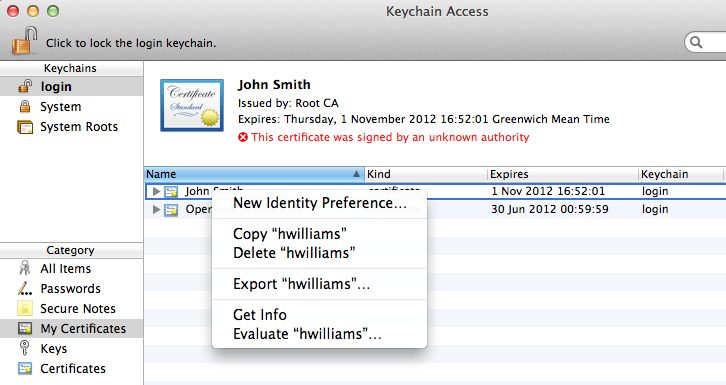
- Right Click on the certificate name and select the "Get Info" item:
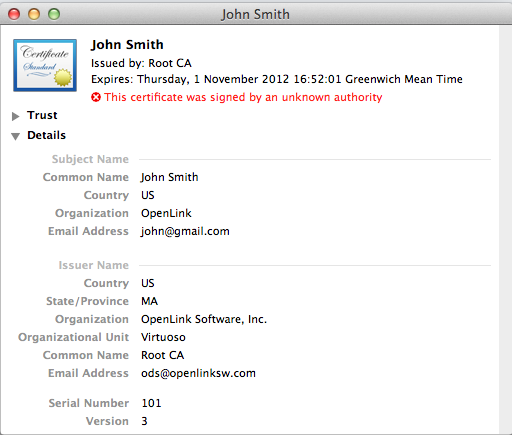
- Expand the tree of the "Trust" item on the left:
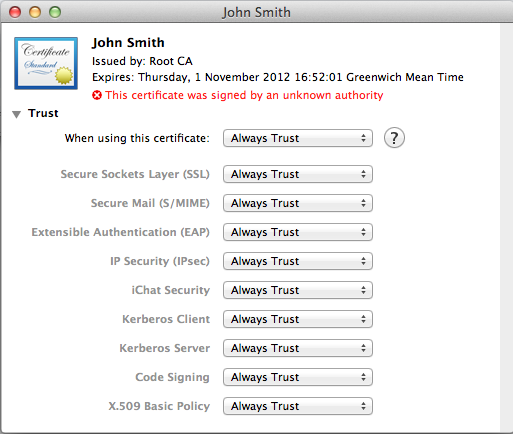
- Set the "when using this certificate" drop down to "Always trust":
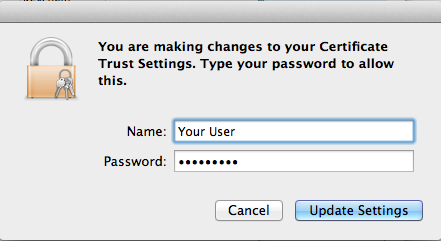
- Enter the password for the user account to authorize the trust change in the key chain:
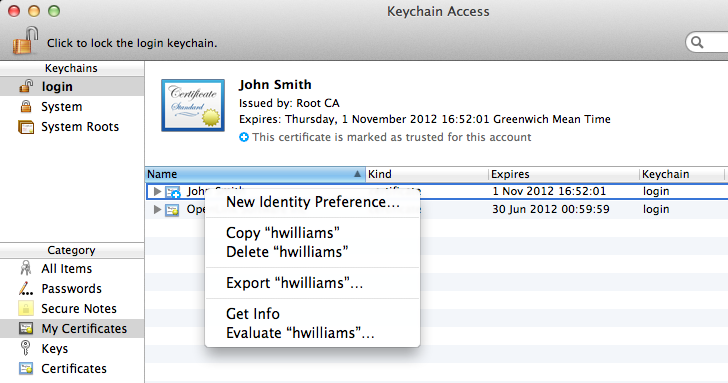
- Right click on the certificate again and select the "New Identity Preference" to the secure HTTP address of the ODS server for ex.
https://id.myopenlink.net/ods and click "Add":
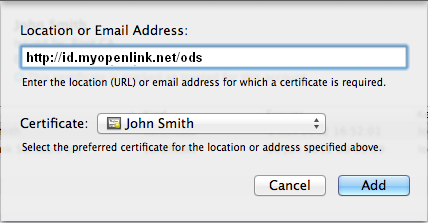
- Go to the "X.509 Certificates" tab of the ODS user account and click on the "Edit" button of the generated certificate:
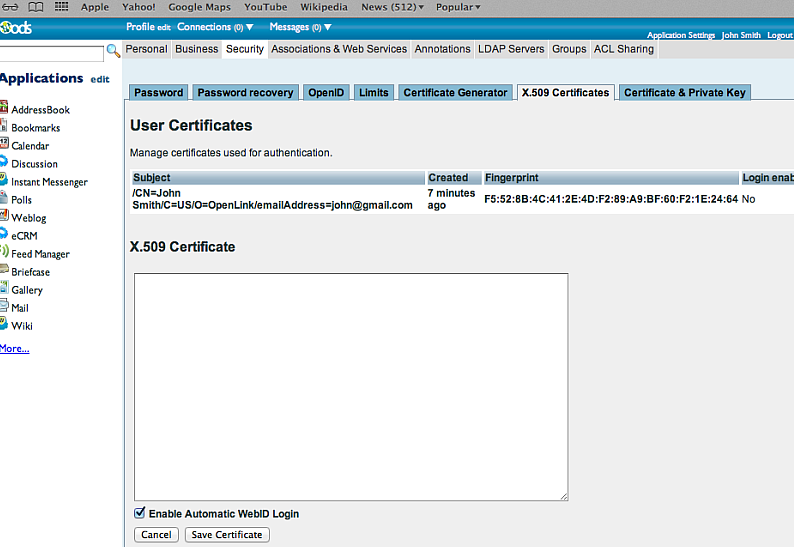
- Select the "Enable Automatic
WebID Login" checkbox and click "Save Certificate" to enable WebID access of this user:
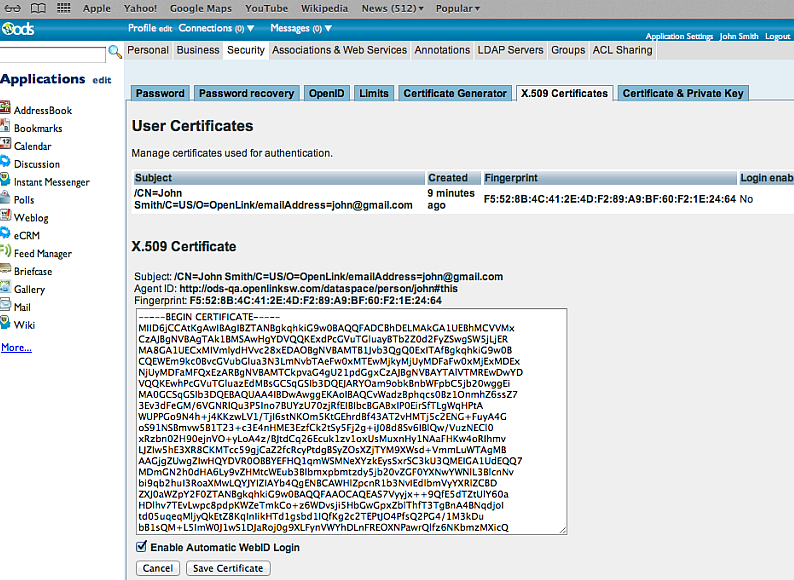
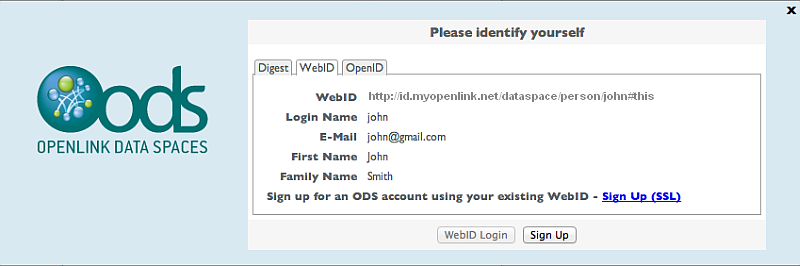
- Log out and access for ex.: https://id.myopenlink.net/ods.
- Select when prompted from your browser, the certificate generated from above.
- The WebID login for the selected user certificate will be presented to enable secure login:
- Perform an WebID based ACL Sharing of a resource to the user with the generated from above X.509 hosted WebID.
Note: these steps apply to any ODS instance.
Related
- Generate an X.509 Certificate (with a WebID watermark) that's managed by host operating system keystore
- Guide of generating X.509 Certificates via ODS
- Safeguarding your Virtuoso-hosted SPARQL Endpoint
- SPARQL Endpoint Protection Methods Collection
- Virtuoso documentation
- Virtuoso Tips and Tricks Collection
- SPARUL over SPARQL using the http://cname:port/sparql-auth endpoint
- Virtuoso Authentication Server UI
- Manage a SPARQL-WebID based Endpoint
- WebID Protocol Support in OpenLink Data Spaces.
- Manage ODS Datadspaces Objects WebID Access Control Lists (ACLs):
- Guide for Set up a X.509 certificate issuer and HTTPS listener and generate ODS user certificates
- Configure Virtuoso+ODS instance as an X.509 Certificate Authority and HTTPS listener
- Configure Virtuoso instance as an X.509 Certificate Authority and HTTPS listener
- Setting up PubSubHub in ODS
- PubSubHubBub Demo Client Example
- Feed subscription via PubSubHub protocol Example
- Setting Up PubSubHub to use WebID Protocol or IP based control lists
- CA Keys Import using Conductor
- Generate an X.509 Certificate (with a WebID watermark) to be managed by a browser-based keystore
- Using Virtuoso's WebID Verification Proxy Service with a WebID-bearing X.509 certificate
- Using Virtuoso's WebID Identity Provider (IdP) Proxy Service with an X.509 certificate
- ODS Briefcase WebID Protocol Share File Guide
- WebID Protocol Specification
- Test WebID Protocol Certificate page
- WebID Protocol Certificate Generation page
