ODS.VirtODSOAuthQA
OAuth QA
MySpace Tools
In order to use the MySpace OAuth Testing Tool:
- Need to have registered myspace account.
- Need to apply to build apps on the MySpace Developer Platform.
Google Tools
Google?s OAuth playground tool can be tried here.
Register your domain in Google
In order to use the tool, you need to register the web application as domain:
- Login at your gmail account
- Go to https://www.google.com/accounts/ManageDomains
- Enter in the field for ex.
the QA server ec2-67-202-42-146.compute-1.amazonaws.com and click the "Add Domain" button.
- Note: for now registered domains cannot be deleted ( not supported from the Google UI)
- As result the domain will be created and the manage domain page will be opened. Here you need to verify you have admin privileges by choosing verification method
- Choose "Upload an HTML file" and follow further the instructions.
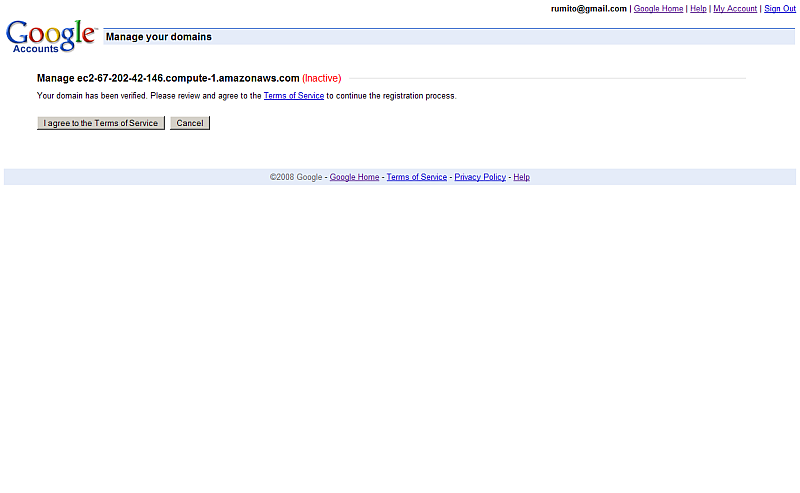
- Once the file is put in the correct server root, you should get the confirmation page:
-
- Click the "Agree .." buttons.
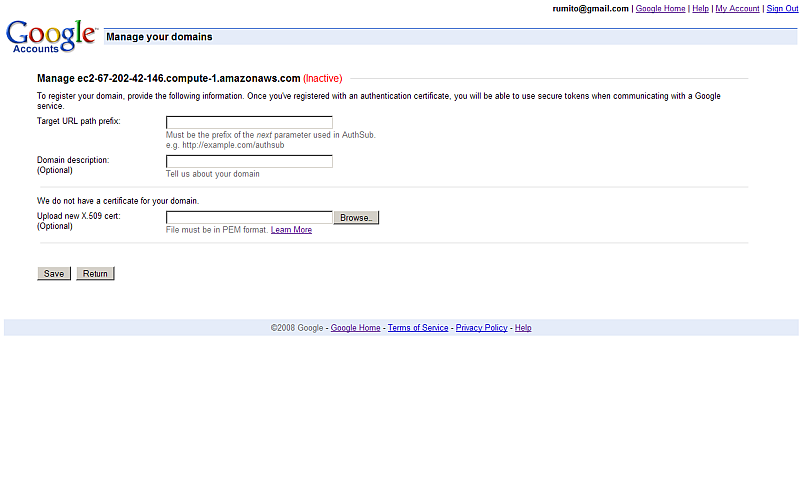
- As result will be additional setting page you need to change.
Type in for "Target URL path prefix:": http://ec2-67-202-42-146.compute-1.amazonaws.com/ods
-
- Click the "Save" button.
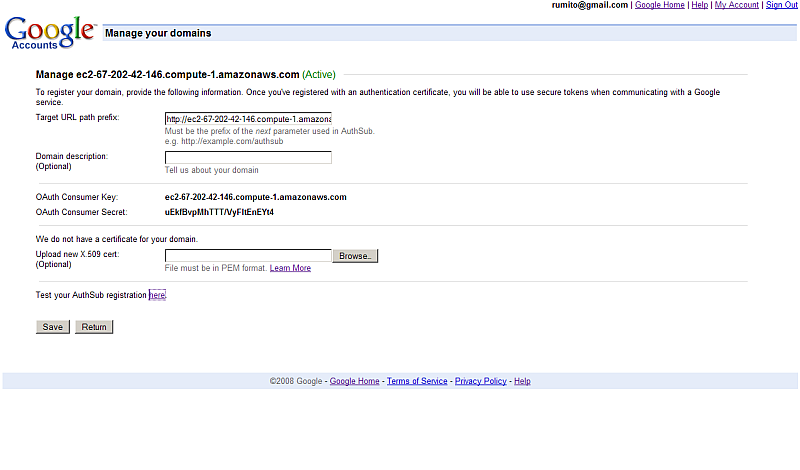
- As result will be shown the generated OAuth Consumer Secret for the OAuth Consumer Key: ec2-67-202-42-146.compute-1.amazonaws.com:
OAuth Consumer Key: ec2-67-202-42-146.compute-1.amazonaws.com OAuth Consumer Secret: uEkfBvpMhTTT/VyFItEnEYt4
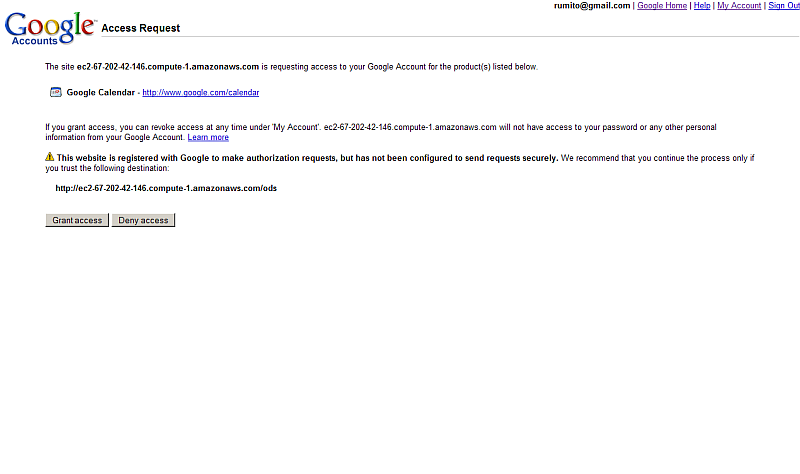
- Also will be shown "test" link "Test your AuthSub registration here". Click it.
- As result will be opened new window with OAuth request
- Click the "Grant Access" button.
-
- As result will be redirected to http://ec2-67-202-42-146.compute-1.amazonaws.com/ods/
- Now lets return to our initial window and click there the button "Save".
- Note that already is shown for the domain that is "Active":
-
The Playground Tool qa steps
Let's try the playground tool:
- Go to http://googlecodesamples.com/oauth_playground/
- Select Scope, for ex. check the check-box for "Blogger".
- Change oauth_signature_method to HMAC-SHA1
- Enter for "oauth_consumer_key": ec2-67-202-42-146.compute-1.amazonaws.com
- Enter for "consumer secret" the value generated from above.
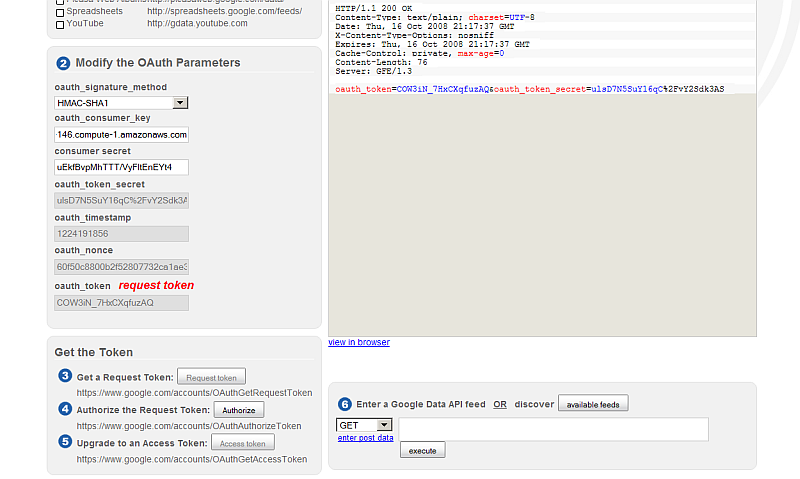
- Click the "Request token" button.
- As result will get Response with Status Ok
-
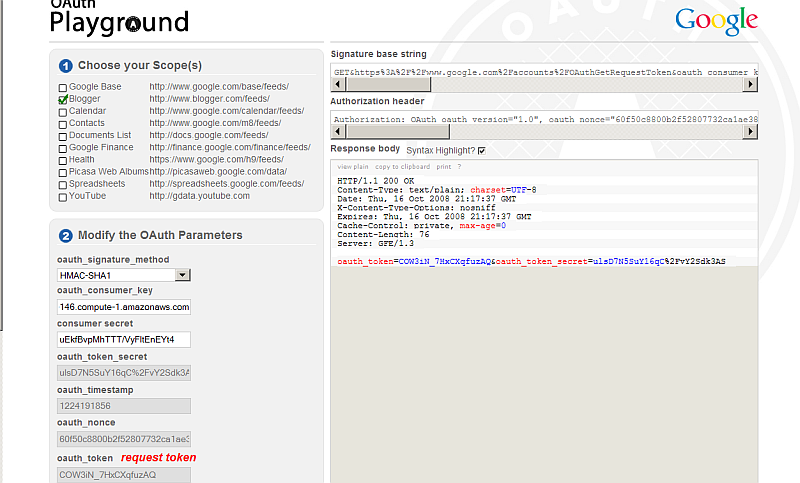
- here is the Signature base string:
GET&https%3A%2F%2Fwww.google.com%2Faccounts%2FOAuthGetRequestToken&oauth_consumer_key %3Dec2-67-202-42-146.compute-.amazonaws.com%26oauth_nonce%3D60f50c8800b2f52807732ca1ae3855ef %26oauth_signature_method%3DHMACSHA1%26oauth_timestamp%3D1224191856%26oauth_version%3D1.0 %26scope%3Dhttp%253A%252F%252Fwww.blogger.com%252Ffeeds%252F
- here is the Authorization header:
Authorization: OAuth oauth_version="1.0", oauth_nonce="60f50c8800b2f52807732ca1ae3855ef", oauth_timestamp="1224191856", oauth_consumer_key="ec2-67-202-42-146.compute-1.amazonaws.com", oauth_signature_method="HMAC-SHA1", oauth_signature="nohPMCw%2BMrO8%2FwslS4oEm2wfuhg%3D"
- here is the Response body:
HTTP/1.1 200 OK Content-Type: text/plain; charset=UTF-8 Date: Thu, 16 Oct 2008 21:17:37 GMT X-Content-Type-Options: nosniff Expires: Thu, 16 Oct 2008 21:17:37 GMT Cache-Control: private, max-age=0 Content-Length: 76 Server: GFE/1.3 oauth_token=COW3iN_7HxCXqfuzAQ&oauth_token_secret=ulsD7N5SuY16qC%2FvY2Sdk3AS
-
- And also in the "Get the Token" section now will be active the "Authorize" button.
Click it.
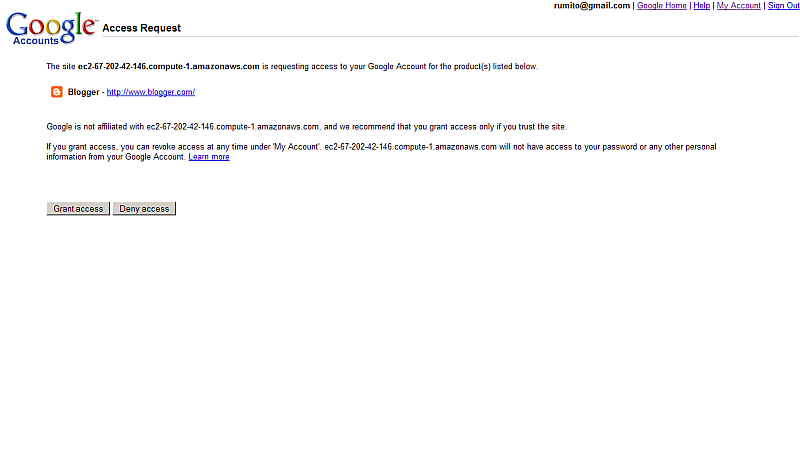
-
- As result will be shown the authentication page where you need to click the "Grant Access" button:
-
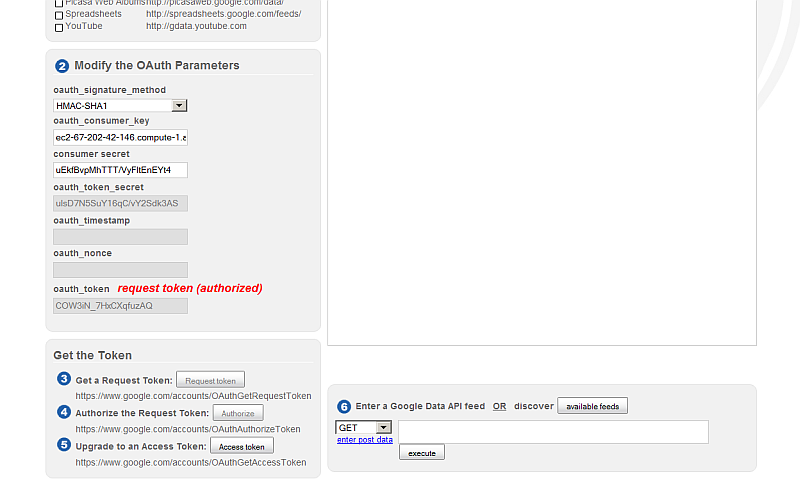
- As result now in the "Get the Token" section will be active the "Access token" button.
Click it.
-
- As result the access_token will be obtained:
-
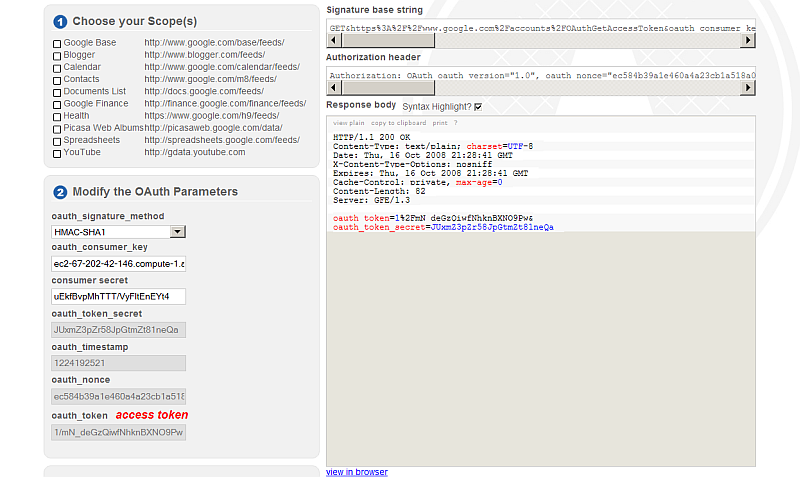
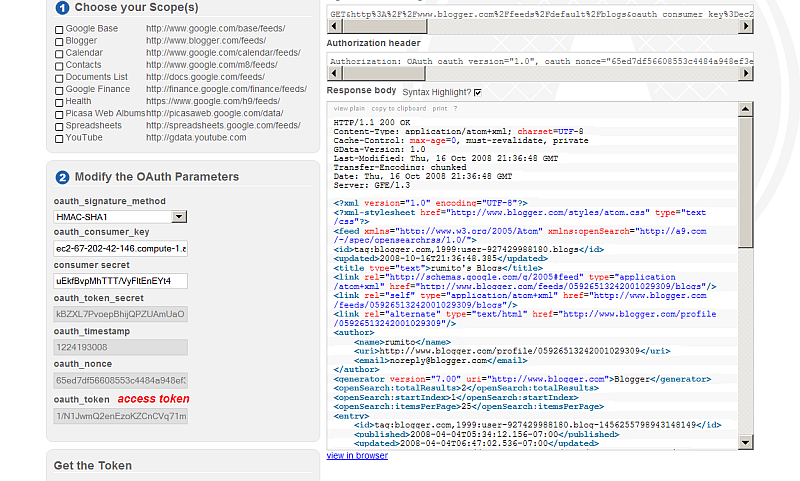
- Click the "available feeds" button marked as 6.
- As result in the "Response" body section will be shown:
Blogger http://www.blogger.com/feeds/default/blogs http://www.blogger.com/feeds/<blogID>/posts/default http://www.blogger.com/feeds/<blogID>/[<postID>]/comments/default
- Copy the 1st URL and paste in the field after the method GET.
- Click "execute".
- As result will find your blogs, post, info at Blogger, surprised? :) :
-
References
- OpenID, OAuth UI and tool links
- Register Web Application in Google as domain
- Google OAuth Playground Tutorial
- OpenLink's explanation of OAuth
- Virtuoso OAuth server
- Using OAuth with ODS
- ODS Ubiquity Commands
- Virtuoso OAuth Implementation
- ODS Controllers
- OAuth Ubiquity Tutorial
- Virtuoso OAuth Test Tool for ODS Controllers
- Virtuoso SPARQL OAuth Tutorial
- ODS Ubiquity Tutorials
- OAuth Applications Authentication examples
- OAuth API
- Virtuoso Authentication Server UI.
- Safeguarding your Virtuoso-hosted SPARQL Endpoint
- SPARQL Endpoint Protection Methods Collection
- Virtuoso documentation
- Virtuoso Tips and Tricks Collection
- SPARUL over SPARQL using the http://cname:port/sparql-auth endpoint
- Manage a SPARQL-WebID based Endpoint
- WebID Protocol Support in OpenLink Data Spaces.
- Manage ODS Datadspaces Objects WebID Access Control Lists (ACLs):
- Guide for Set up a X.509 certificate issuer and HTTPS listener and generate ODS user certificates.
- Setting up PubSubHub in ODS
- PubSubHubBub Demo Client Example
- Feed subscription via PubSubHub protocol Example
- Setting Up PubSubHub to use WebID Protocol or IP based control lists
- CA Keys Import using Conductor
- Generate an X.509 Certificate hosted WebID Guide
- Generate an X.509 Certificate (with a WebID watermark) to be managed by host operating system keystore
- Generate an X.509 Certificate (with a WebID watermark) to be managed by a browser-based keystore
- Using Virtuoso's WebID Verification Proxy Service with a WebID-bearing X.509 certificate
- Using Virtuoso's WebID Identity Provider (IdP) Proxy Service with an X.509 certificate
- ODS Briefcase WebID Protocol Share File Guide
- WebID Protocol Specification
- Test WebID Protocol Certificate page
- WebID Protocol Certificate Generation page